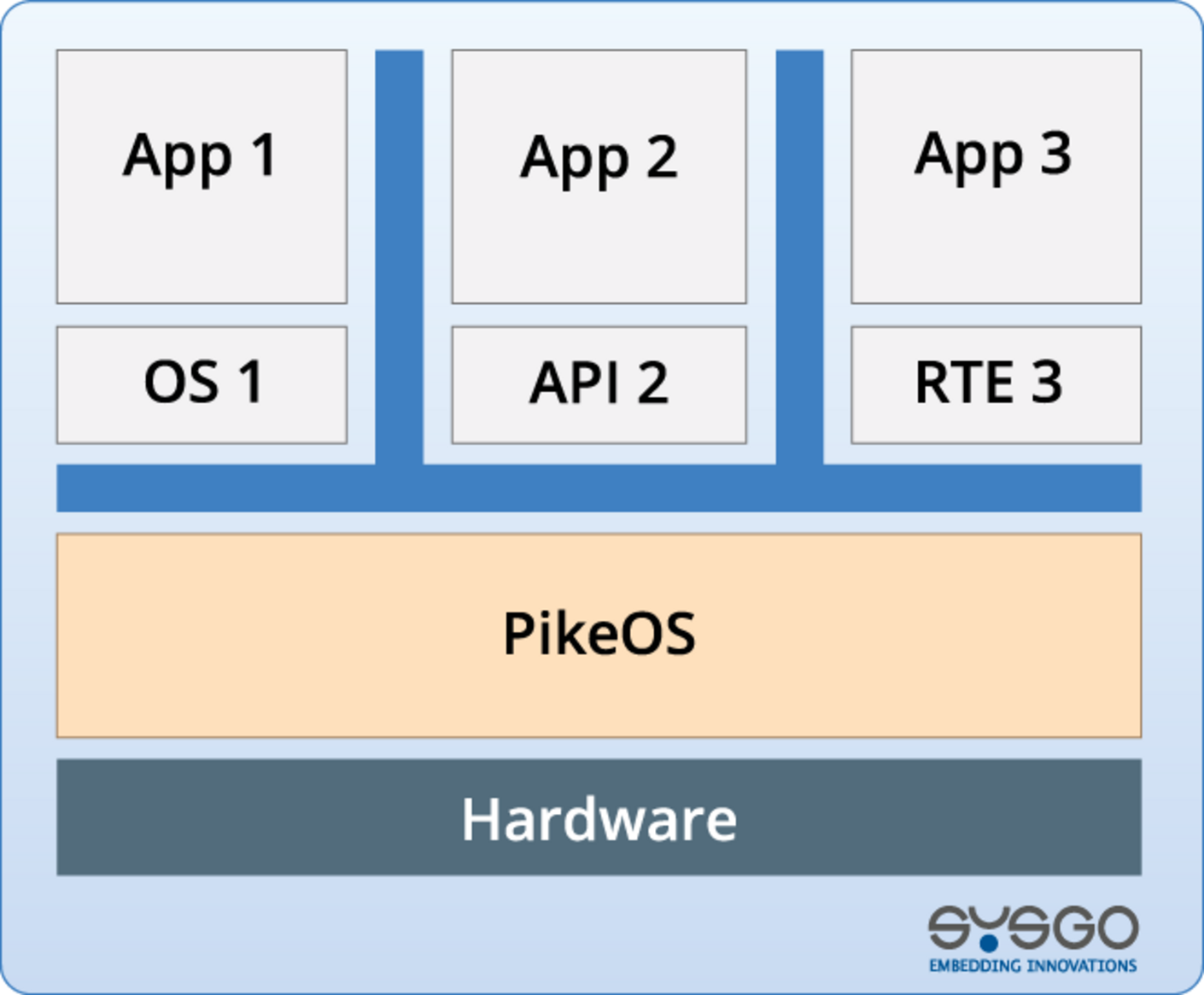
PikeOS is pre-certified on highest Safety certification levels per industry
Our PikeOS product roadmap aligns to the latest certification standards as they appear
SYSGO offers pre-certified components, such as CIP, CFS or CML to reduce time of system certification
SYSGO directly works with well known certification authorities, such as TUEV (TÜV) or BSI (Federal Cyber Security Authority). Customers can rely on this relationship
More than 75% of SYSGO engineering staff has experiences in certification projects
Certification Kits are available as standard, for authority or for BSP creation
We offer Safety bulletins to inform customers about vulnerabilities