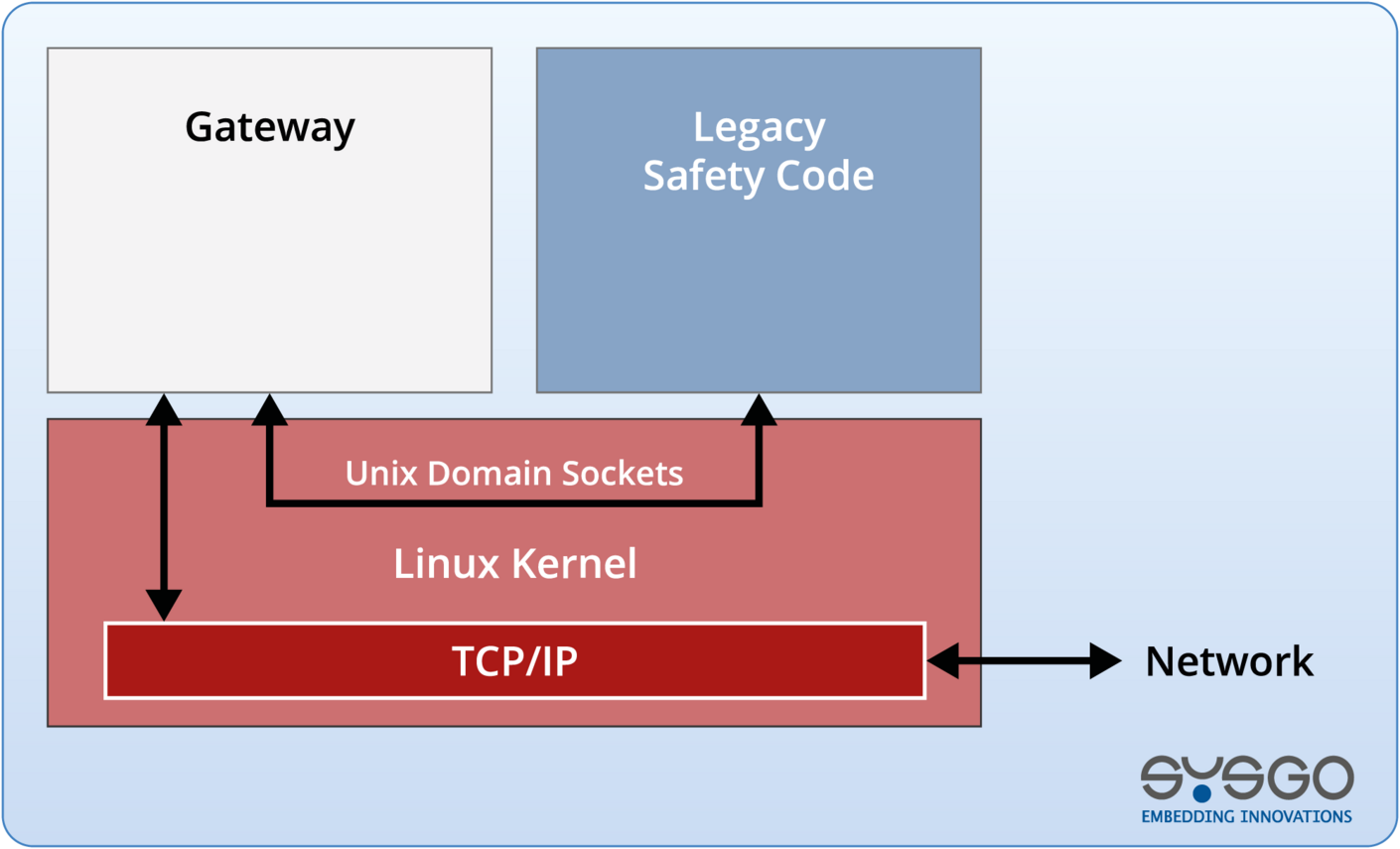
Secure & Connected Vehicle Platforms
SYSGO provides a reference architecture for the Automotive domain, focusing on:
- Protection of internal vehicle networks and fieldbus systems
- Secure external communication (V2X, cloud backend)
- Safe and secure over-the-air (OTA) software updates
- Based on PikeOS for RTOS partitioning and ELinOS for rich Linux functionality
For more information, see the SACoP Product Page