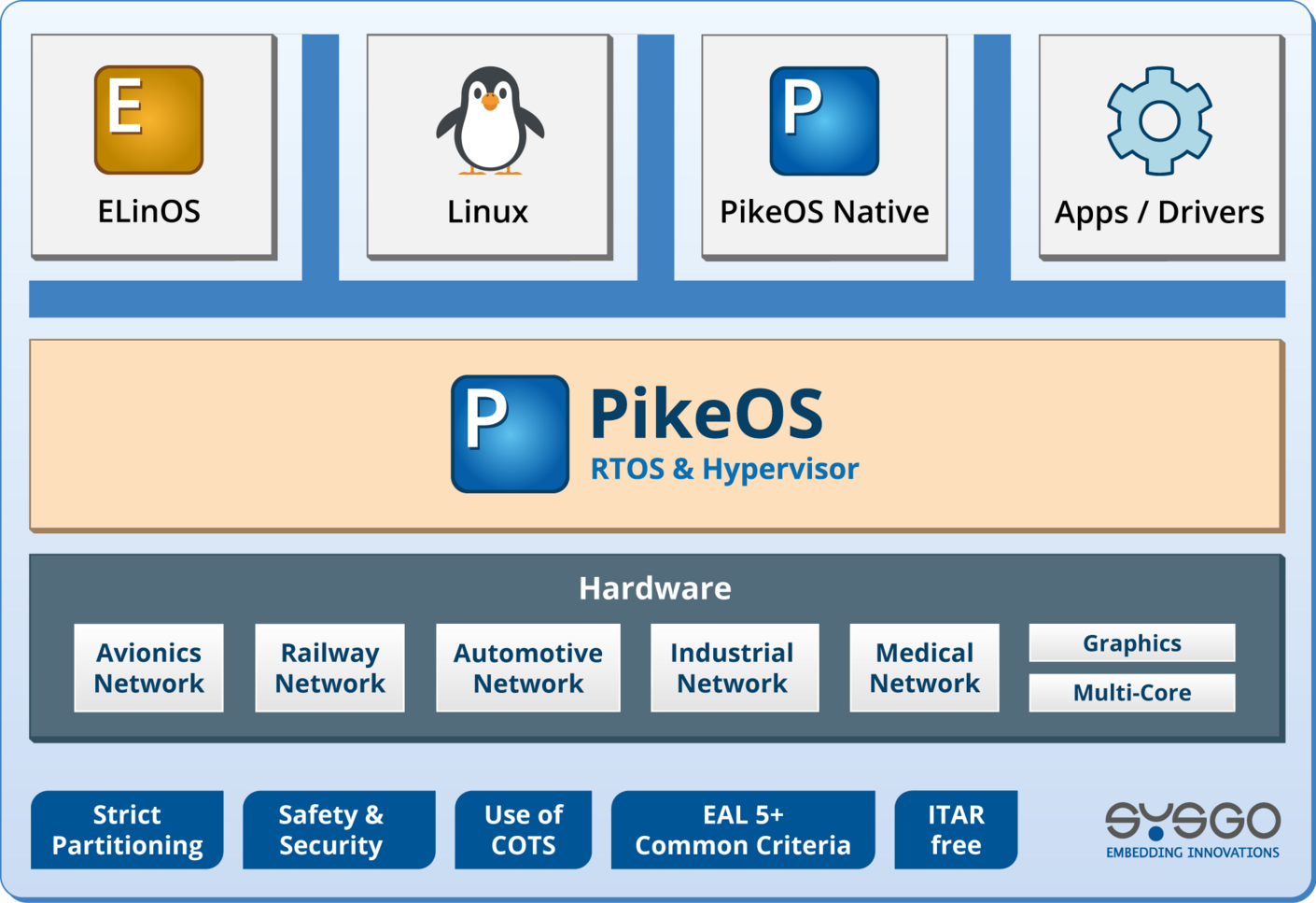
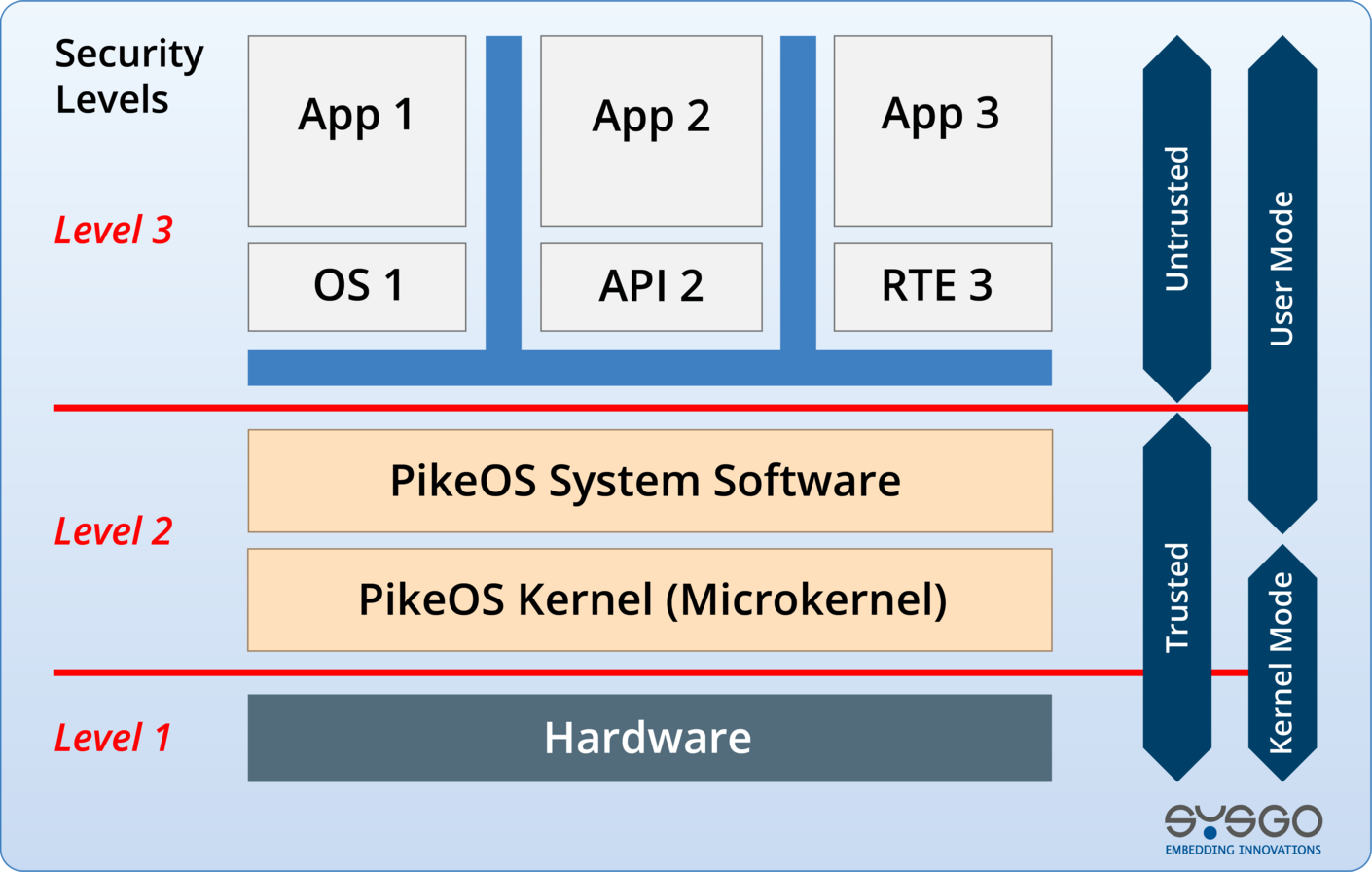
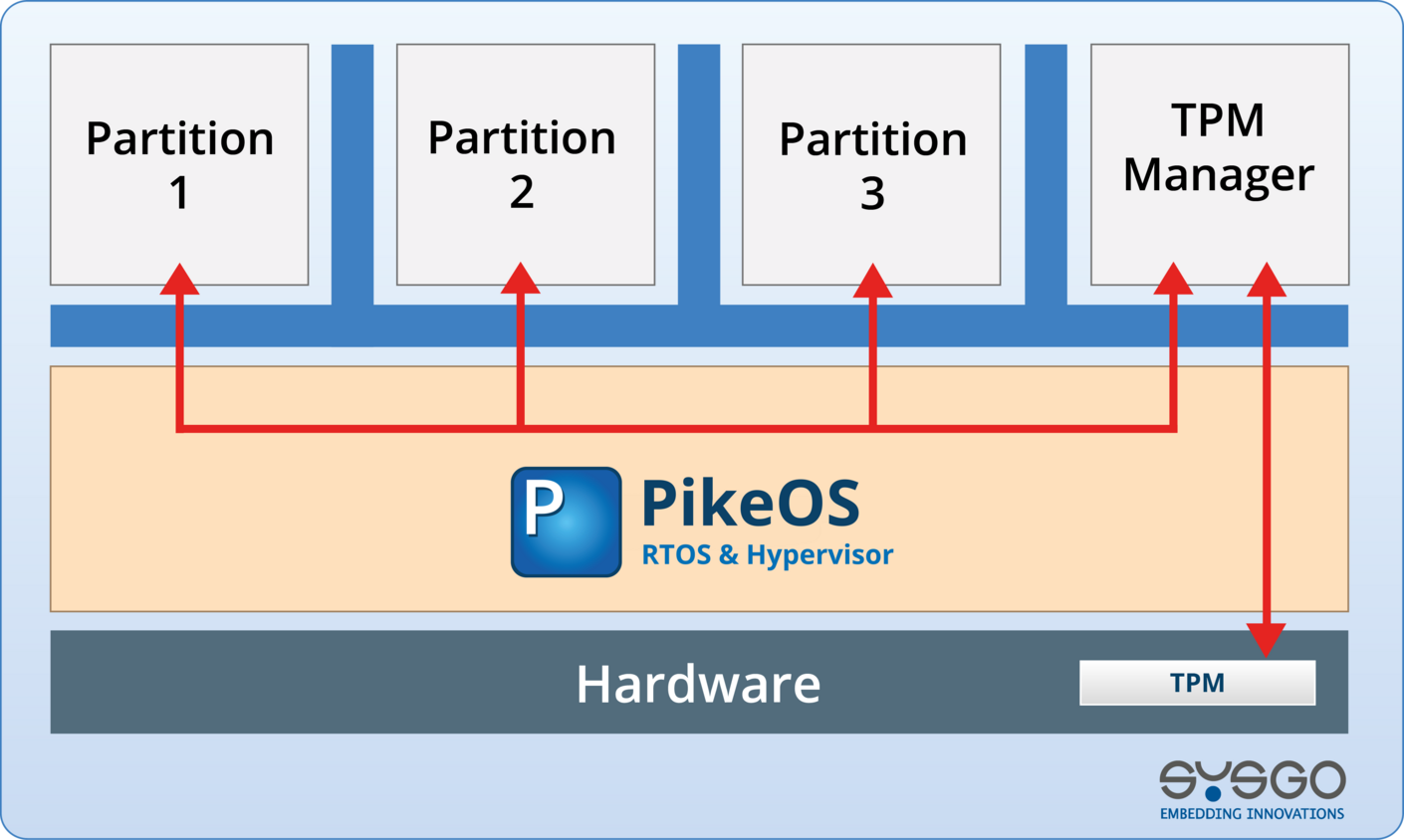
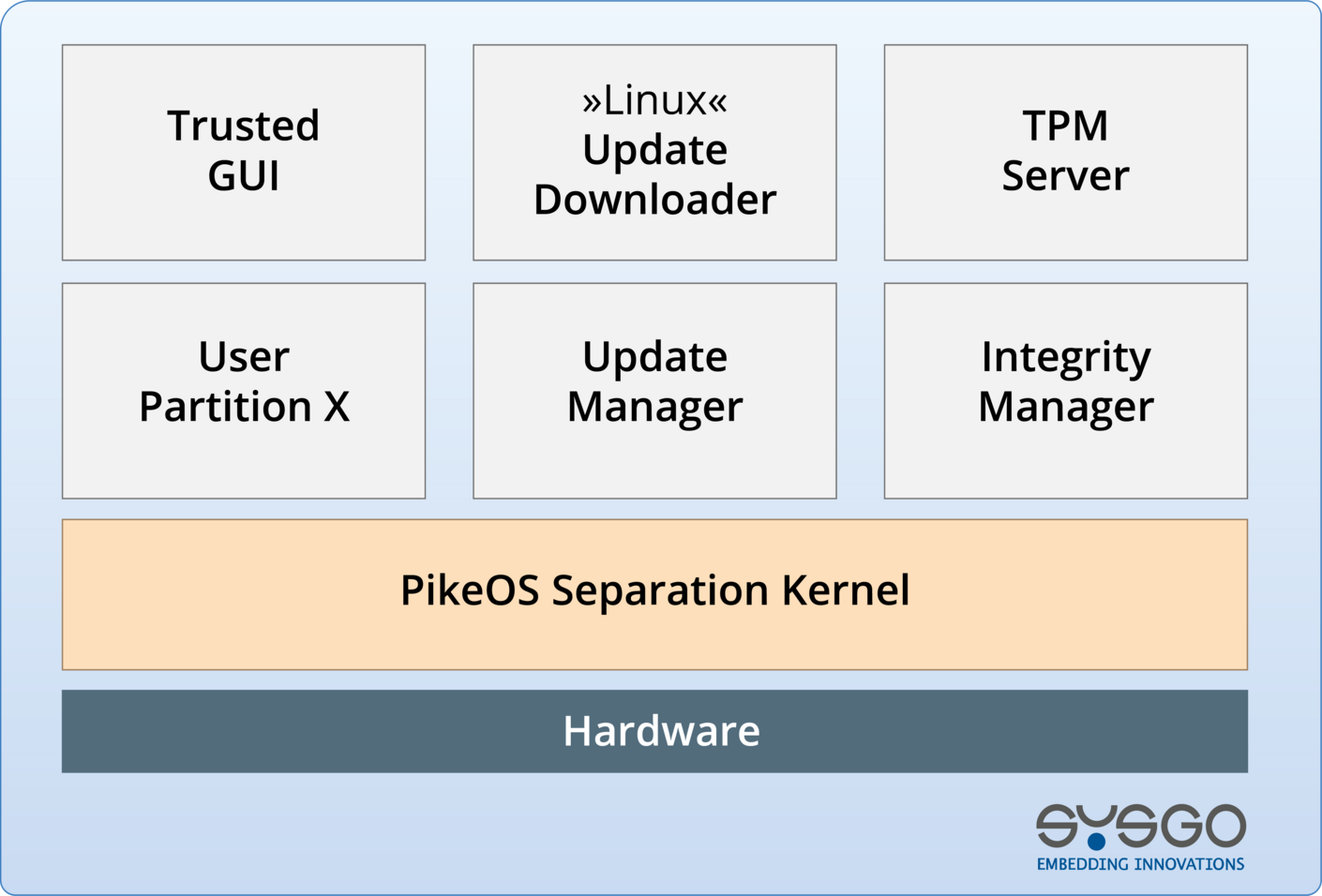
Secure-by-Design
Architected with Security-first principles, including deterministic prevention of remote code execution
Security-approved Hardware and Components
Support for TPM (Trusted Platform Module), HSM (Hardware Security Module), and certified hardware to build a strong root of trust
Secure Boot Cycle
Ensures only verified and signed code is executed from power-on to runtime
Root of Trust Establishment
Hardware-based trust anchors for measured boot and secure identities
Over-the-Air Software Updates
Encrypted and integrity-checked OTA updates to keep systems secure in the field
Integrated Firewall and Network Protection
Add Defense-in-depth with IP filtering and secure protocol stacks
Security Event Monitoring
Built-in support for logging and monitoring critical Security events at runtime
Secure Middleware and Connectivity
The SYSGO platform includes secure connectivity stacks and middleware for modern embedded networking
Integrated Secure Connectivity
SYSGO platform with secure connectivity middleware available
Flexible Bundles with 3rd-Party Security Components
Integrates easily with leading Security tools and libraries to accelerate innovation and certification